The term virus has come across a long adventure within the digital world. Being evolved for replicating programs, to begin with, the virus or extraordinary malware or adware have become a headache for digital customers around the globe.
The virus assaults are completed for monetary purposes however sometimes the sole motive would possibly vary. There are different sorts of viruses in the form of malware, adware, or spyware.
Microsoft Windows is maximum susceptible to viruses because of its full-size user base across the globe.
To save such viruses from getting into your gadget, there are anti-virus programs. those applications first delimit the virus and include them, however in case the virus has already infected the pc they can even neutralize them.
Furthermore, the Anti Virus producers have long past a step in advance and now offer full-evidence security software programs.
It reduces the chances of having infected with the aid of introducing new protection rules and completely secures the community.
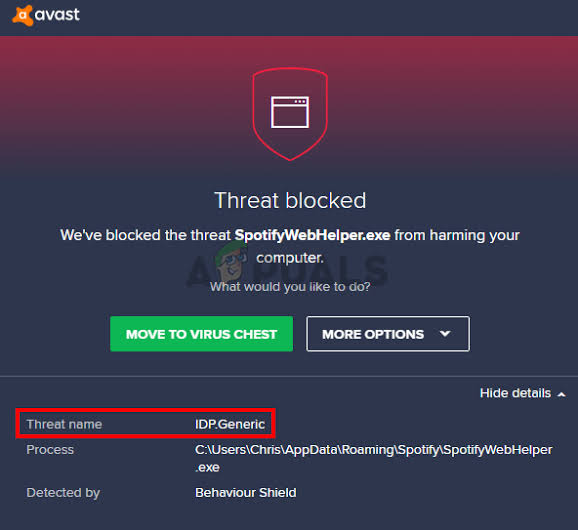
The danger isn’t restricted to a single report, however, it’ll affect plenty of files.IDP.generic danger is a detection file this is designed to detect a worm virus. in case you don’t apprehend what a worm is, it’s malicious code that looks reliable.
However the identical can take control of your laptop. those codes are designed to steal your data out of your computer or different devices in the community.
Trojan horse viruses usually may be visible on crack software programs, and you will by no means understand that it’s, to begin with, a pandemic. but as soon as you install it, it’s going to start hacking your information.
There are distinctive types of trojan horse viruses. some of them encompass Info stealer Trojan, sport-thief Trojan, fake AV Trojan, Downloader Trojan, distributed Denial of carrier (DDoS) attack Trojan, Rootkit Trojan, remote get entry to Trojan, Backdoor Trojan, Ransom Trojan, Mailfinder Trojan, Trojan IM, Trojan banker, an SMS Trojan. We would like to explain those exclusive Trojans sorts, however, it isn’t the right article to describe the identical.
Symptoms
- The overall performance of your pc will slow down.
- Your laptop will crash every time.
- Any other one is pop-up windows, which arise regularly.
- Your pc will now not perform adore it used to first of all.
- Random spam software program established up for the duration of windows startup.
- Several unsolicited mail emails may be despatched out of your laptop to an unknown cop.
- The virus might also hack your stored passwords. regularly other accounts will be a chance.
- You’ll lose your statistics, and you may be asked to pay to retrieve those files. Precautions which you need to comply with.
As we said, these viruses more often than not come from cracked video games that you download online.
It can additionally be from portions of the song, snapshots, and films that you men download from unknown assets. in the end, it could also be from junk mail emails and websites that you open.
Protect your pc from affecting those styles of viruses, you can follow these strategies.
- Set up any antivirus which protects you and permits firewall protection. in case your laptop is strolling on home windows 10, then home windows Defender itself is enough.
- Avoid downloading software from risky websites. usually, download from professional websites and boards like XDA.
- In the case you need to apply pirate software, then use any anti-spyware software to test for viruses on set up the software program.
- Never open any attachments that you receive via spam emails. additionally, just delete those junk mail emails without commencing them.
- Continually replace your home windows with the modern-day version along with the Home windows Defender or your third-party Antivirus software program.
- never download songs, movies, and different kinds of stuff from dangerous websites.
- Uninstall cracked packages that you have downloaded from dangerous websites.

The usage of Malware bytes unfastened model
For this, first, download the software program from their authentic internet site.
As soon as it has been downloaded, install the same on your pc. it will ask for permissions to adjust the machine, and also you have to allow that.
There may be many on-display instructions, and you may install them using following the one’s things. The setup will ask if it’s your work pc or private computer.
Choose in step with your desire after which keep the setup system.
as soon as this system opens, Tap at the Get started button to begin the method. it’s going to ask which will choose among free and top class versions.
You can buy the premium model if you can manage to pay for it. however, for our use, the free version is more than enough. So tap on the free button.
Now tap the test button to start scanning, and the application will experiment with the whole files on your pc.
Like every other app, it’s going to take some time to experiment with the whole record. It’ll show a lock button if it has located any viruses after reviewing. faucet on the equal to delete the one’s viruses. it’s going to delete the malicious files and registry keys.
Restart your laptop to complete the system.
Hitman Pro
You can use the equal to scan for malware and other unwanted applications
As the call indicates, it’s a pro application that you want to purchase. but, you could experiment with matters without the pro model. And in case you men locate any viruses for your device, you may dispose of the identical through activating the trial for 30 days.
You could download Hitman Pro.
Like the above technique, deploy the same for your laptop.
follow the on-screen instructions and in the end tap on next to start scanning.
wait for a couple of minutes to complete the test and then faucet on next to eliminate the malicious files.
you could set off the unfastened license for 30 days from here.
After activating the free license, it will start the method of putting off one’s documents.
Restart your computer after the technique ends.
Always be Updated with us visit GeeksULTD for Real-time Updates.